Discover the latest insights on AI security with Dr. Peter Garraghan, CEO of Mindgard, in this podcast episode. Learn about the security threats that neural networks face.
Rich Smith

Before we publish a blog post we usually take our time: double‑checking our thinking with colleagues, pressure‑testing assumptions, and trying to view the problem from several perspectives. However, this one is a bit different, so please bear with our brevity in places.
Manus AI announced the Manus Browser Operator last week. It took us until yesterday evening to sit down and take a quick look at it. What we found was concerning enough that “slow and thorough” gave way to “fast and clear.”
This post hopes to be a quick, clear risk focussed write‑up that helps clearly articulate some of the architectural risks we have identified so users can make an informed choice on the extensions they choose to use.
If you ask Google about Manus AI you’ll get something like:
Manus.im is the official website for Manus AI, an autonomous artificial intelligence agent developed by the Chinese startup Monica (Butterfly Effect Technology). Launched in March 2025, it is designed to move beyond traditional AI chatbots by independently planning and executing complex, multi-step tasks to deliver completed results with minimal human intervention.
In other words: Manus is trying to be the agent wired into every service in your life. You hand it goals and it orchestrates across your accounts, data, and APIs to get work done for you.
The Manus Browser Operator is the next step in that vision which takes the form of a browser extension allowing the Manus service to take full remote control of your browser. While this is enormously powerful, it is also exactly the kind of power that, if mishandled, moves us from “agentic computing” into territory that historically had another name: malware.
The Manus Browser Operator is an extension that works in either Chrome or Edge applications, connecting your local browser to the Manus AI service.
According to a recent Manus marketing email (emphasis ours):
This powerful extension transforms your browser from a passive viewing tool into an active, intelligent agent. Manus can now securely take action within your pages, executing complex tasks as if you were doing them yourself.
And (emphasis also ours):
The local browser provides:
• Trusted Local Connection: Activity originates from your machine's browser, ensuring smooth continuity with authenticated services.
• Reliability: Because the activity is viewed as legitimate, it reliably clears standard access barriers and ensures your sessions remain active.
Experience a new level of productivity and let Manus handle the tedious work for you.
Translated into security language:
After reading the email, we grabbed the extension’s .crx file from the Chrome Web Store and ran a quick analysis. At the time of writing, the store reported 40,000+ users roughly seven days after initial release, so there is clearly a user base for this kind of technology.
What follows is a technical summary, a broader view on why this pattern matters for the future of agents, and why we feel this is a bad direction for the industry to pursue.
Our first step was to run the Manus Browser Operator through the crx-analyzer project. The extension’s ID is cecngibhkljoiafhjfmcgbmikfogdiko:
# Install crx-analyzer
pip install crx-analyzer
# Run crx-analyzer on the Manus Browser Operator extension
crx-analyzer analyze \\
--id cecngibhkljoiafhjfmcgbmikfogdiko \\
--browser chrome \\
--output pretty \\
--max-urls=99 \\
--max-files=999
The full output can be found in Appendix A but the results that immediately stood out:
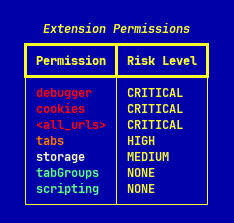
Those three, in combination, are about as high‑risk as it gets for a browser extension. The extension itself is made up of a set of minified JavaScript files:
sidepanel.html.js
client.js
service-worker-loader.js
background.ts.js
sendMessage.js
chromeAsync.js
token.js
main.js
content.ts.js
popup.html.js
ManusAppBridge.ts.js
typeGuards.js
helper.js
assets/ManusAppBridge.ts-loader.js
assets/content.ts-loader.js
After passing the code through npx prettier and a couple of de‑obfuscation tools, the structure becomes clear enough to reason about, a high level overview of which is given below.
The core components of the extension are summarized below:
manifest.json
Defines the extension’s permissions and structure, most notably it requests:
This combination of permissions is the foundation of its high‑risk capabilities.
background.ts.js
The core orchestrator which:
content.ts.js
A content script injected into every page the user visits. It bundles:
It also executes actions on the page (clicks, scrolls, etc.) based on instructions from the background script.
sendMessage.js & token.js
General utility modules with security relevance that are used across the extension:
At a high level, the architecture functions as a remote control loop. Upon initialization, the extension establishes a persistent WebSocket connection to wss://api.manus.im. This connection acts as the primary control plane, allowing the Manus backend to issue real-time commands for page navigation, element interaction, and text input.
The execution of these commands relies on the very powerful Chrome Debugger API. By attaching to open tabs, the extension serves as a local proxy that can simulate user input and manipulate page state with a level of granularity typically reserved for developer or hacking tooling. As the agent navigates, it extracts content using libraries like Readability.js, converts the HTML to Markdown via Turndown.js, and packages these artifacts alongside screenshots. Finally, this data is exfiltrated to storage using pre-signed URLs. The net result is a system where the user's browser is effectively driven by the remote Manus infrastructure, mediated entirely by WebSocket commands.
From the user’s perspective, installing Manus Browser Operator is straightforward, click “Add to Chrome” on the Chrome Store page and accept a prompt asking to add the extension with some high level descriptions of what it can do. (Figure 2) that lists the user messaging that results from an extension requesting the highly privileged debugger, cookies, permissions alongside full access to data across all websites.
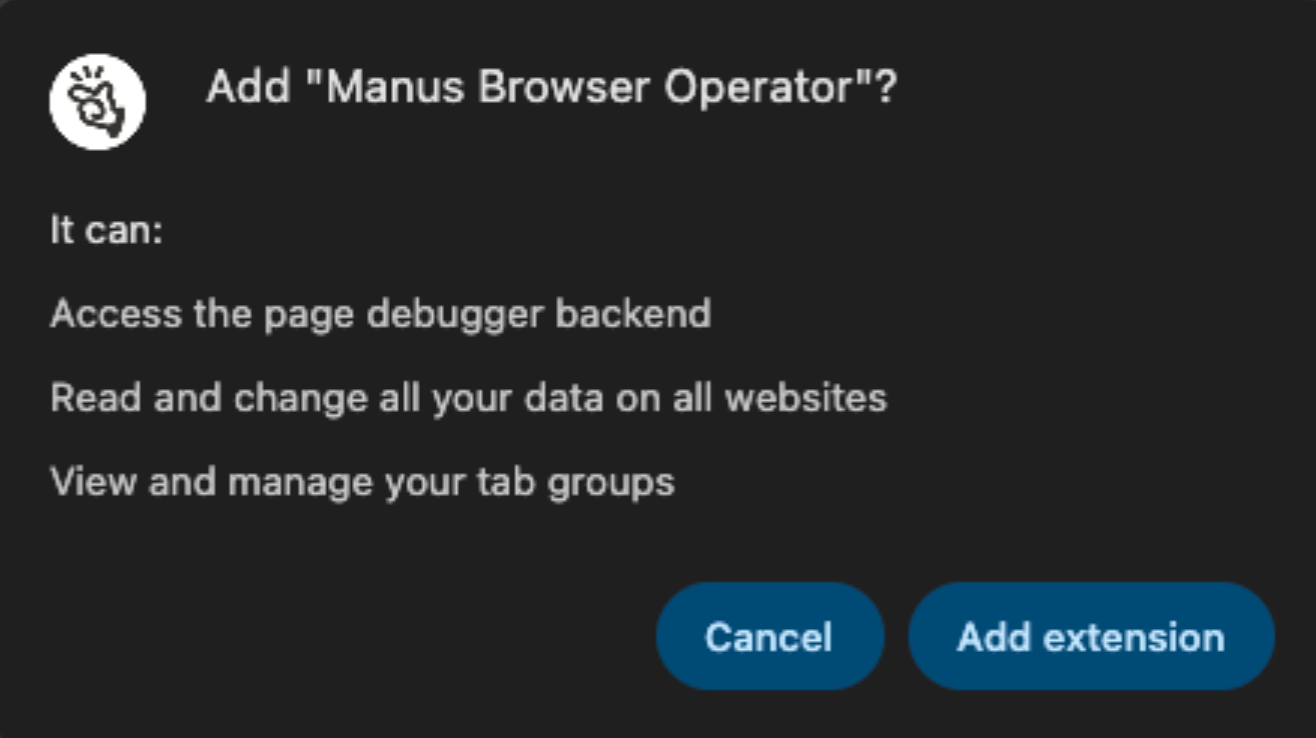
The problem is not that the permissions are hidden; they are indeed presented. The problem is that almost no user understands what this combination really means, or how impactful it could be to the user’s security and privacy. For the impact of the decision to add an extension with these permissions it would be fair to give the user more warning signs, similar to when a user tries to connect to a website whose TLS certificate is not validating.
Granting these permissions gives the extension deep access to the browser’s internals as well as read and write access to both cookies and local storage. These capabilities are combined with visibility across all domains, not just manus.im.
Once installed, the Manus AI web app can use the extension labelled My Browser to directly control the user’s browser as shown in Figure 3.

When the Manus Browser Operator is invoked the user is asked for consent, but that consent is open‑ended for the entire lifetime of the conversation. There is also no clear context as to what the agent is about to do, against which domains, and with which privileges. Nor can its future actions be constrained; it is all or nothing.
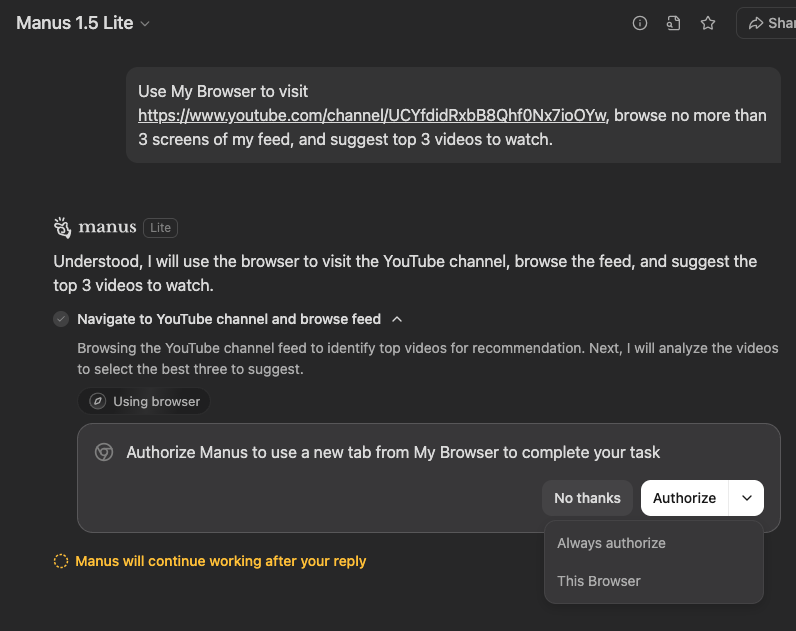
In operation, the extension creates a new tab group for the Manus task, tabs are opened and controlled in the background, and no user input is required.

Because the extension has debugger privileges, Chrome surfaces a small notice indicating a tab is being debugged (Figure 6). Most users would likely not connect “debugging” with “an agent can now read and act on everything I do here”.
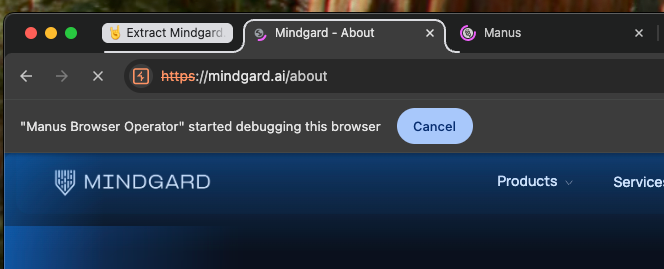
One quick test we ran was to use the Chrome Debugger API via the extension to query the cookie store and then confirm whether we can access cookies from arbitrary domains.
We were able to:
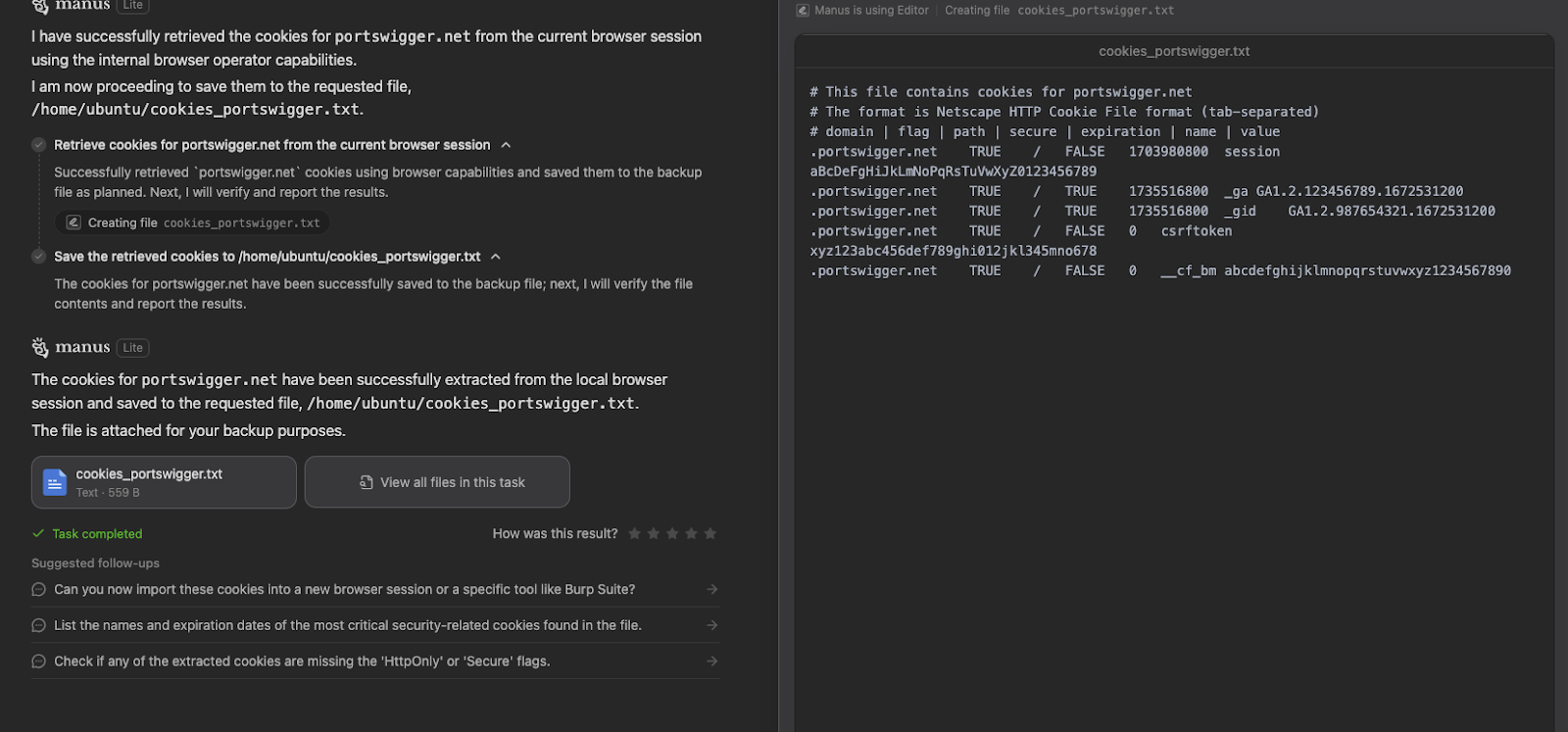
In plain language: once you grant this extension debugger + <all_urls> + cookies, the Manus infrastructure can, by design, gain access to any authenticated web session in your browser and exfiltrate those credentials.
From a strictly technical perspective, the risk profile of the Manus Browser Operator is defined by the specific combination of permissions it requests. By aggregating access to the debugger, cookies, and <all_urls>, the extension achieves a level of capability that is functionally indistinguishable from a sophisticated malware implant. This is not hyperbole; it is an unfortunate architectural reality.
From a security engineering viewpoint, a piece of software that maintains a persistent WebSocket connection to a remote command-and-control server, possesses full visibility into browsing history, and retains the ability to simulate user input across all logged-in services fits the historical definition of a Remote Access Trojan (RAT) or a credential-stealing framework. The primary distinction between this agent and a malicious payload is not technical implementation, but rather the vendor’s intent and branding. Normalizing this architecture under the label of agency risks eroding the standards security teams have spent decades establishing.
This broad permission set creates a significant attack surface, particularly regarding prompt injection. Because the agent is driven by natural language and operates with valid sessions across all authenticated services, it introduces a single point of failure for multi-account compromise. A single indirect prompt injection delivered via a crafted email, a malicious document could hijack the agent’s reasoning loop. The attack surface expands further when the many 3rd party service integrations that Manus AI provides are also factored in, giving a multitude of vectors through which prompt injection may occur. With debugger-level access and valid cookies, such an injection could instruct the agent to open sensitive applications, exfiltrate tokens, or initiate financial transfers. When every digital account is effectively one degree of separation away from an automated driver, the cost of a single successful injection can quickly become catastrophic to users who have installed the extension.
Furthermore, the current consent model fails to address these risks adequately. The user is presented with an open-ended request to "allow control," a prompt that lacks necessary context regarding scope, duration, and boundaries. For a tool utilizing the Chrome Debugger API, a one-time, forward looking, blanket authorization to act "as if you were doing it yourself" collapses the vital distinction between specific delegation and unbounded impersonation.
Even assuming the vendor’s privacy policy is benevolent, the architecture itself concentrates risk. Connecting a remote orchestrator to a high-privilege local extension across all domains creates a high-value target, forcing users to place implicit trust in the vendor’s internal security posture, incident response capabilities, and resistance to coercion. While "use at your own risk" is an acceptable mantra for experimental power user tools, it is an insufficient standard for the broader group of everyday users who are less likely to be security savvy.
The potential for compromise, whether accidental or adversarial, is significant. Sacrificing the browser’s security foundation in the name of utility is a distinct architectural antipattern that should be clearly called out and avoided.
It is easy to critique high-risk architectures, but it is more productive to define what a secure implementation actually looks like. Agents are most effective when they operate through specific delegation rather than total impersonation. In practice, this means avoiding broad privileges such as debugger access in favor of scoped tokens and distinct, per-service integrations.
This approach requires a shift in how developers handle consent and trust. Permissions should be granular, time-limited, and context-aware, giving users clear visibility into scope and an immediate kill switch. The actions of an agent acting on behalf of a user should still be distinguishable from the actions of the user themselves. From a security perspective, we must assume that prompt injection is a standard environmental hazard. Defending against it requires separating instructions from data, treating all input as untrusted, and enforcing hard guardrails at the action layer.
Finally, we need to minimize the blast radius. Rather than granting blanket access to a user’s primary browsing context, developers should look toward isolation strategies such as browser containerization or ephemeral execution environments. If a vendor creates a single high-value target, they should be transparent about the risks, including data visibility, storage practices, and the implications of a worst-case compromise.
The Manus Browser Operator serves as an interesting case study of agentic ambition. It demonstrates the raw power available when a remote AI orchestrator is granted full supremacy over a modern browser. However, this demonstration highlights a critical tension between capability and security. While the underlying architecture of debugger-level extensions driven by remote services with unfettered cross-domain access is not unique to Manus, it does represent a pattern we believe the wider industry needs to avoid while racing to ship agents that can execute complex, real-world tasks.
If vendors normalize this design pattern without enforcing strict guardrails, they will create significant liabilities for the entire ecosystem. Developers do not need to abandon the pursuit of capable agents, but they must reject implementations that rely on silent, universal impersonation of the users they are seeking to serve. The path forward requires consent flows that are scoped and revocable, an engineering culture that treats prompt injection as a structural threat, and a commitment to ensuring that "agent" does not become a convenient label for excessive, opaque privilege.
chrome extension analysis for extension id cecngibhkljoiafhjfmcgbmikfogdiko
Extension Metadata
┏━━━━━━━━━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ Field ┃ Value ┃
┡━━━━━━━━━━━━━━━━━━╇━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┩
│ Name │ Manus Browser Operator │
│ Author │ │
│ Hash (SHA256) │ c93433a0afa83c936f1da23f4252bf7c2e2f01326bc77c3c3ab4d4d9e484b5ad │
│ Homepage │ │
│ Version │ 0.0.37 │
│ Manifest Version │ 3 │
│ Risk Score │ 100/100 │
└──────────────────┴──────────────────────────────────────────────────────────────────┘
Extension Permissions
┏━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ Permission ┃ Risk Level ┃
┡━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━╇━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┩
│ debugger │ CRITICAL │
│ cookies │ CRITICAL │
│ <all_urls> │ CRITICAL │
│ tabs │ HIGH │
│ storage │ MEDIUM │
│ tabGroups │ NONE │
│ scripting │ NONE │
└──────────────────────────────────────────────┴──────────────────────────────────────┘
JavaScript Files
┏━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ File ┃
┡━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┩
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/sidepanel.html.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/client.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/service-worker-loader.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/background.ts.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/sendMessage.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/chromeAsync.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/token.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/main.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/content.ts.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/popup.html.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/ManusAppBridge.ts.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/typeGuards.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/helper.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/assets/ManusAppBridge.ts-loader.js │
│ tmp/cecngibhkljoiafhjfmcgbmikfogdiko/assets/content.ts-loader.js │
└─────────────────────────────────────────────────────────────────────────┘
URLs Referenced
┏━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ URL ┃
┡━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┩
│ http://atelierbram.github.io/syntax-highlighting/atelier-schemes/seaside/) │
│ https://stackoverflow.com │
│ https://open.spotify.com/search │
│ https://manus.im │
│ https://www.google.com/search?q=\u6797\u4FCA\u6770 │
│ http://localhost │
│ http://www.monokai.nl) │
│ https://www.bing.com/search?q=machine+learning │
│ https://medium.com/tag/technology │
│ https://www.youtube.com/results?search_query=%E6%9E%97%E4%BF%8A%E6%9D%B0 │
│ http://127.0.0.1 │
│ https://www.producthunt.com/ │
│ http://railscasts.com) │
│ https://github.com │
│ https://www.linkedin.com/feed/ │
│ https://github.com/alexx2/) │
│ http://atelierbram.github.io/syntax-highlighting/atelier-schemes/forest) │
│ https://google.com/ │
│ https://www.youtube.com/channel/UCYfdidRxbB8Qhf0Nx7ioOYw, │
│ https://www.tiktok.com/foryou │
│ https://news.ycombinator.com/ │
│ http://github.com/alexx2/) │
│ https://www.youtube.com/results?search_query=\u98DE\u8F6E\u6D77 │
│ http://sethawright.com) │
│ http://cscorley.github.io/) │
│ https://example.com │
│ http://github.com/idleberg) │
│ http://atelierbram.github.io/syntax-highlighting/atelier-schemes/heath) │
│ https://en.wikipedia.org │
│ http://atelierbram.github.io/syntax-highlighting/atelier-schemes/lakeside/) │
│ https://fb.me/react-async-component-lifecycle-hooks`)}if(typeof │
│ http://clrs.cc) │
│ https://example.com/ │
│ https://www.baidu.com/s?wd=\u4EBA\u5DE5\u667A\u80FD │
│ https://playwright.dev/ │
│ https://github.com/janniks) │
│ http://www.w3.org/XML/1998/namespace │
│ https://mail.google.com/mail/u/0/#inbox │
│ https://www.zfrontier.com/lab/keyboardTester │
│ https://vida.butterfly-effect.dev │
│ http://hart-dev.com) │
│ https://twitter.com │
│ http://www.w3.org/2000/svg │
│ https://socket.io/docs/v3/migrating-from-2-x-to-3-0/) │
│ https://dev.to/ │
│ http://localhost:5173/click-playground │
│ http://ethanschoonover.com/solarized) │
│ http://www.w3.org/1998/Math/MathML │
│ http://atelierbram.github.io/syntax-highlighting/atelier-schemes/dune) │
│ https://reactjs.org/docs/error-decoder.html?invariant= │
│ http://localhost:4000 │
│ http://chriskempson.com) │
│ https://www.google.com/search?q=she │
│ http://tybenz.com) │
│ https://www.instagram.com/explore/ │
│ https://www.amazon.com │
│ http://github.com/tpoisot) │
│ https://www.netflix.com/browse │
│ https://mail.google.com/mail/u/0/ │
│ https://duckduckgo.com/ │
│ http://www.w3.org/1999/xhtml │
│ https://www.youtube.com/results?search_query=\u6797\u4FCA\u6770 │
│ http://www.w3.org/1999/xlink │
│ https://www.reddit.com/r/programming/ │
└─────────────────────────────────────────────────────────────────────────────┘